In today’s digital landscape, where cyberattacks and data breaches are increasingly common, protecting sensitive information is paramount for any organization. This is where ISO 27001 comes in—the international benchmark for information security management. If you’re looking to safeguard your company’s data and client information, understanding this standard is crucial.
What is ISO 27001?
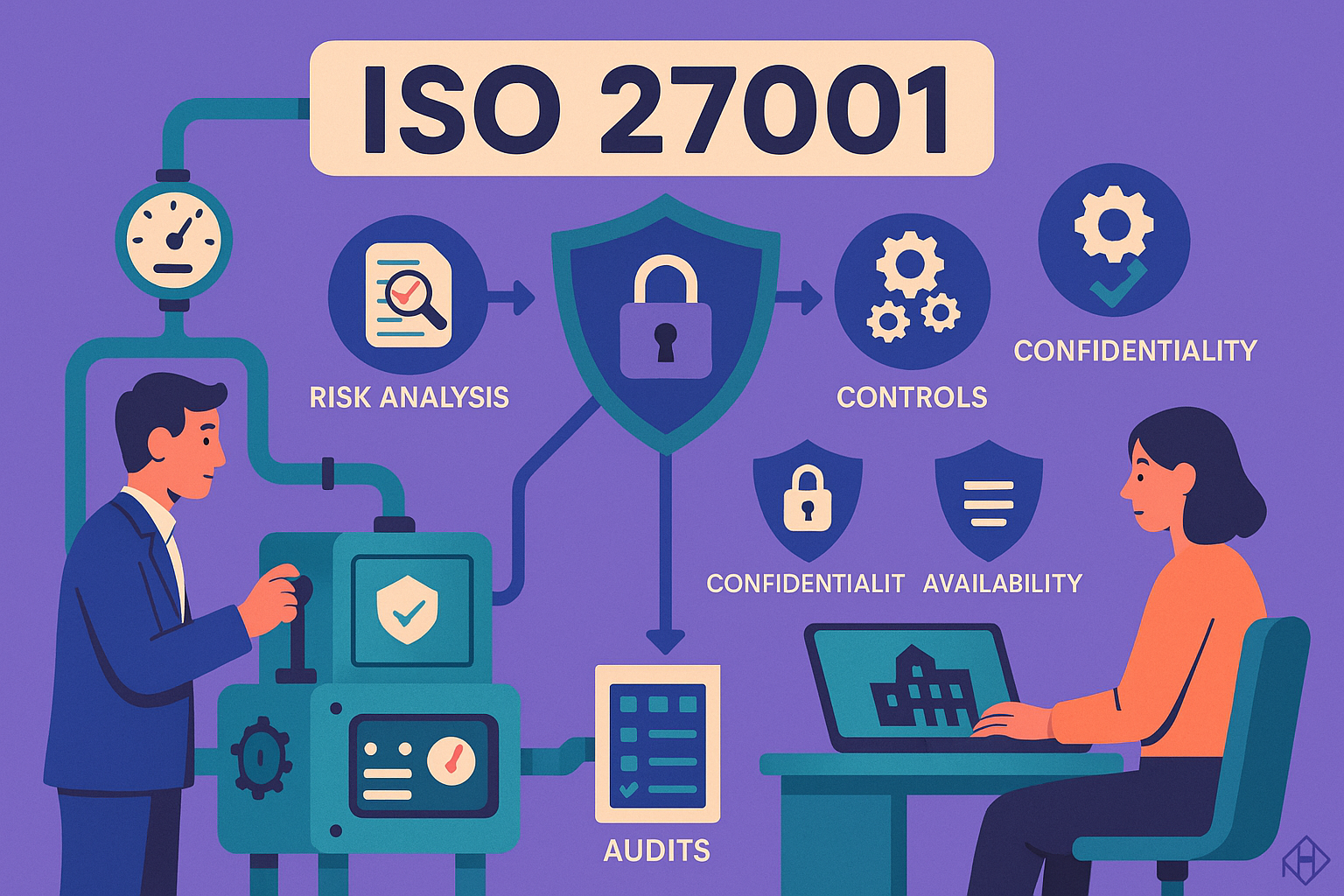
ISO 27001 is an international standard designed to help organizations establish, maintain, and continually improve an Information Security Management System (ISMS). In essence, it provides a structured framework for companies to identify, assess, treat, and monitor risks related to the security of their information systems, implementing effective measures to protect them.
Why is ISO 27001 Essential?
Certification to ISO 27001 serves as a strong assurance of an organization’s commitment to information security. It demonstrates that your organization is proactive and reliable in managing security risks, distinguishing you from competitors. Built on the principle of continuous improvement, it ensures your security posture evolves with new threats. Beyond being a significant competitive advantage, ISO 27001 compliance also facilitates adherence to other legal frameworks such as NIS2, GDPR, and DORA, streamlining your regulatory efforts.
How Does ISO 27001 Work?
ISO 27001 is built upon three core principles of information security:
- Confidentiality: Ensuring that sensitive data is protected from unauthorized access.
- Integrity: Guaranteeing that information is neither modified nor corrupted, maintaining its accuracy and completeness.
- Availability: Making sure that data is accessible to authorized users when needed.
To ensure comprehensive security, the standard mandates a structured approach, often referred to as the PDCA (Plan-Do-Check-Act) cycle:
Step-by-Step Implementation of ISO 27001
- Risk Analysis:
- Identify: Begin by identifying potential threats and vulnerabilities within your organizational context and for a clearly defined scope of information systems. This involves understanding your assets, their value, and potential attack vectors.
- Assess: Evaluate the likelihood and impact of these risks to prioritize them.
- Implementation of Controls:
- ISO 27001’s Annex A outlines 93 best practices, categorized into four key areas, to mitigate identified risks:
- Organizational Measures: Policies, procedures, roles, and responsibilities for information security.
- Technical Measures: Controls related to IT systems, networks, access management, encryption, and malware protection.
- Physical Measures: Security of physical premises, equipment, and storage media.
- Personnel Measures: Employee training, awareness, background checks, and disciplinary processes.
- ISO 27001’s Annex A outlines 93 best practices, categorized into four key areas, to mitigate identified risks:
- Regular Audits:
- Conduct internal and external audits periodically to verify that the ISMS is functioning effectively and continuously improving. This step is crucial for maintaining certification and adapting to new security challenges.
Obtaining Certification
Achieving ISO 27001 certification is a significant asset for any organization, demonstrating a robust commitment to information security. For individuals looking to contribute to this process and advance their careers, specialized training courses are available to help you understand and effectively implement this standard. These courses provide the knowledge and skills necessary to prepare an organization for certification and maintain compliance over time.
🔍 Discover Kaptan Data Solutions — your partner for medical-physics data science & QA!
We're a French startup dedicated to building innovative web applications for medical physics, and quality assurance (QA).
Our mission: provide hospitals, cancer centers and dosimetry labs with powerful, intuitive and compliant tools that streamline beam-data acquisition, analysis and reporting.
🌐 Explore all our medical-physics services and tech updates
💻 Test our ready-to-use QA dashboards online
Our expertise covers:
🔬 Patient-specific dosimetry and image QA (EPID, portal dosimetry)
📈 Statistical Process Control (SPC) & anomaly detection for beam data
🤖 Automated QA workflows with n8n + AI agents (predictive maintenance)
📑 DICOM-RT / HL7 compliant reporting and audit trails
Leveraging advanced Python analytics and n8n orchestration, we help physicists automate routine QA, detect drifts early and generate regulatory-ready PDFs in one click.
Ready to boost treatment quality and uptime? Let’s discuss your linac challenges and design a tailor-made solution!
Get in touch to discuss your specific requirements and discover how our tailor-made solutions can help you unlock the value of your data, make informed decisions, and boost operational performance!
Comments